
Padding Oracle Attack on PKCS#1 v1.5: Can Non-standard Implementation Act as a Shelter? | springerprofessional.de
![Systems, apparatuses and methods for a signal extension padding scheme Patent Grant Sun , et al. March 9, 2 [NXP USA, Inc.] Systems, apparatuses and methods for a signal extension padding scheme Patent Grant Sun , et al. March 9, 2 [NXP USA, Inc.]](https://uspto.report/patent/grant/10944502/US10944502-20210309-D00000.png)
Systems, apparatuses and methods for a signal extension padding scheme Patent Grant Sun , et al. March 9, 2 [NXP USA, Inc.]
Types of Cartilage Vector Illustration. Labeled Educational Tissue Scheme. Stock Vector - Illustration of bone, cellular: 164166812
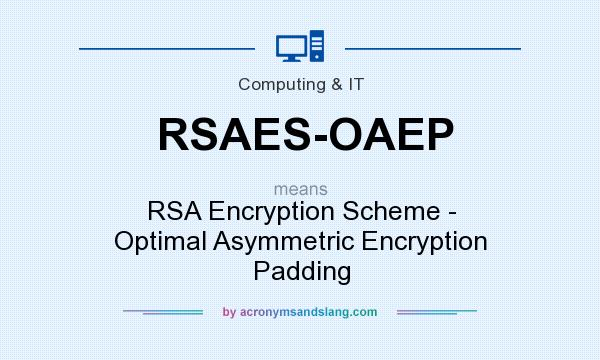
RSAES-OAEP - "RSA Encryption Scheme - Optimal Asymmetric Encryption Padding" by AcronymsAndSlang.com

C# static code analysis | cwe: Encryption algorithms should be used with secure mode and padding scheme

Masking scheme for sampling different-length samples. Top: processing a... | Download Scientific Diagram
Signal Extensions: Zero-Padding, Symmetrization, and Smooth Padding :: Advanced Concepts (Wavelet Toolbox)

C# static code analysis | cwe: Encryption algorithms should be used with secure mode and padding scheme

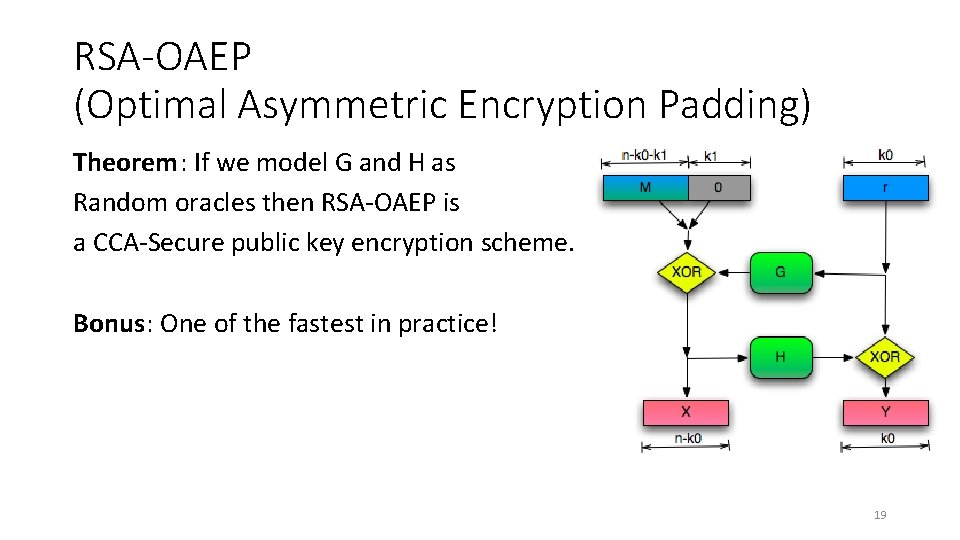




![Block Ciphers - Java Cryptography [Book] Block Ciphers - Java Cryptography [Book]](https://www.oreilly.com/library/view/java-cryptography/1565924029/httpatomoreillycomsourceoreillyimages2081165.png)

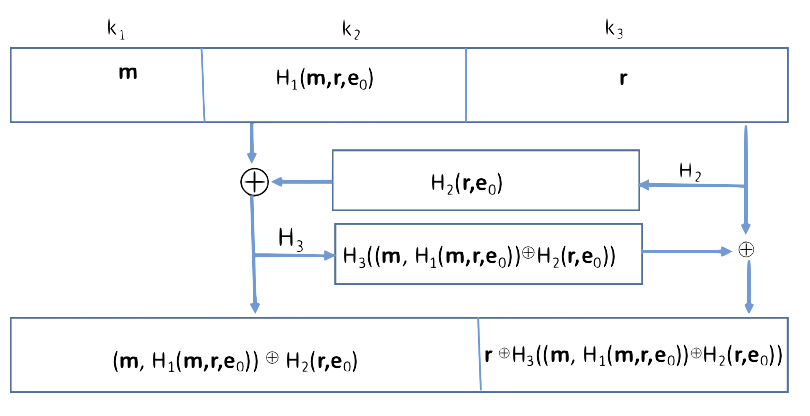
![PDF] A novel chaotic encryption scheme based on pseudorandom bit padding | Semantic Scholar PDF] A novel chaotic encryption scheme based on pseudorandom bit padding | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/aba1a9777b97d22f736d740e4f7dbf7153fa0005/3-Figure2-1.png)
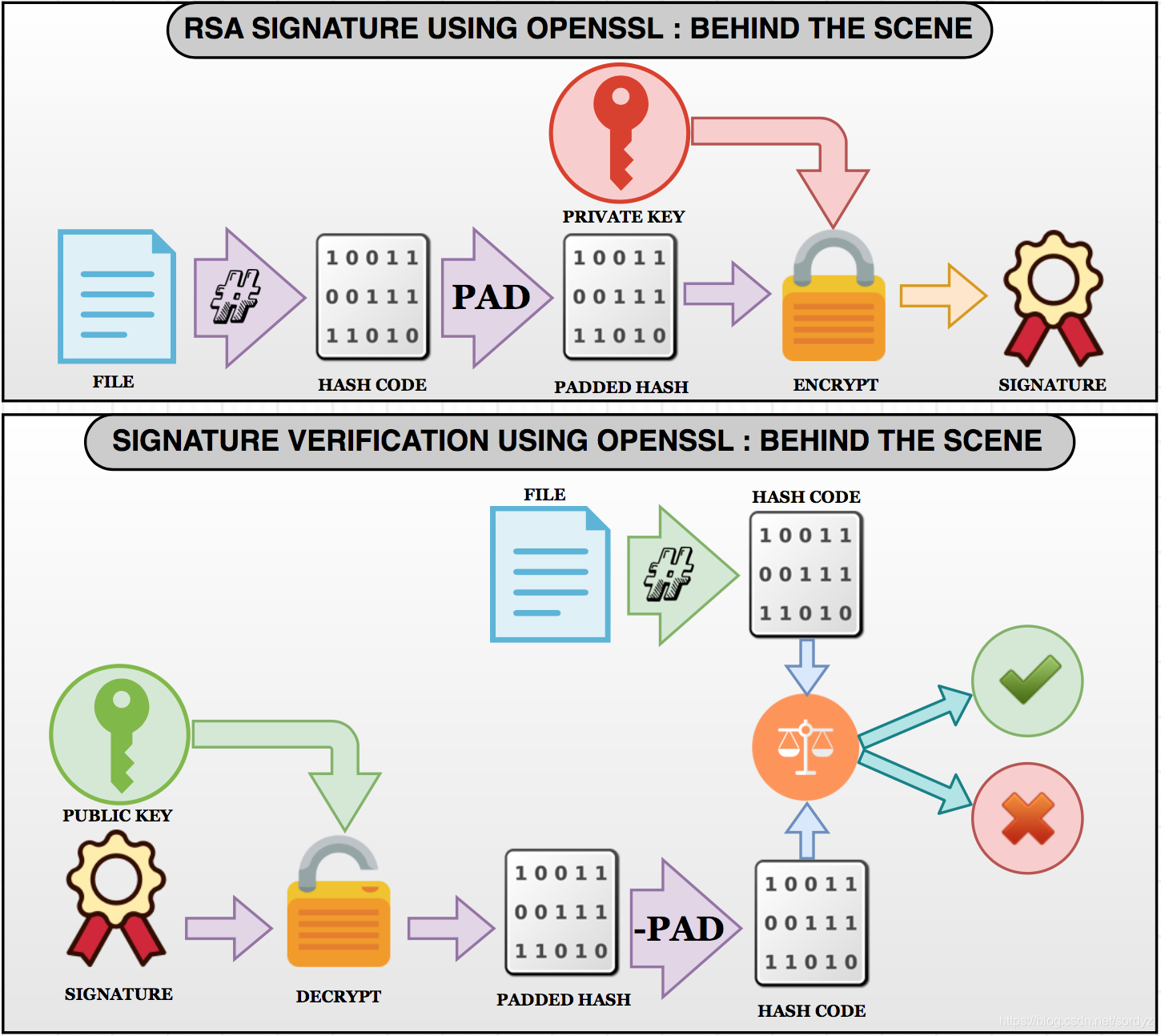


![PDF] Versatile padding schemes for joint signature and encryption | Semantic Scholar PDF] Versatile padding schemes for joint signature and encryption | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/0988eddbd5dc293ac23447de74c54e4d1c41267e/3-Figure1-1.png)